One of quantum cryptography protocols which is most spread now is BB84 protocol. In the given protocol one-photon statuses may be modulated on polarization or on a relative phase. Each of these modulation methods has the advantages and lacks. In particular, polarizing modulation is most preferable at data transfer on open optical channel while modulation on a relative phase may be used in fibre-optical communication systems.
In this work efficiency of quantum cryptography protocol BB84 with coding one-photon statuses on polarization is researched. With this purpose was developedt software complex for computer which allows taking into account both parameters of transmitting and reception units, and parameters of quantum data link. At photons sequence generating on transmitting unit in model two situations are possible:
- The amount of photons of optical impulse duration is strictly fixed. The given situation allows to estimate efficiency of the protocol at ideal one-photon or multiphoton laser usage.
- The amount of photons for duration of optical impulse is accidentally and is subordinate to Poisson law with given average
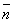 . Thus generation of pseudorandom numbers n, having Poisson distribution with average
. Thus generation of pseudorandom numbers n, having Poisson distribution with average 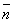 , was carried out using method offered by Caen. During simulation the analysis of this algorithm [1] was spent. The sequence of random variables generated thus has expectation and a dispersion distinguished from value
, was carried out using method offered by Caen. During simulation the analysis of this algorithm [1] was spent. The sequence of random variables generated thus has expectation and a dispersion distinguished from value 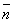 on the 100-th long of percent. It confirms legitimacy of offered algorithm usage under law of Poisson random numbers generation.
on the 100-th long of percent. It confirms legitimacy of offered algorithm usage under law of Poisson random numbers generation.
As parameter of the photoreception unit its quantum efficiency describing probability of optical into electrical signal conversion used. Given parameter, along with noise properties od photo-recieving equipment, is one of defining efficiency of all communication system.
At simulation optical radiation quantum data link losses with absorption and scattering of radiation were taken into an account. Also, situation with presence in the channel of intercepting agent was modelled. Thus two situations were researched:
- Interception and generation by the malefactor of all photons for optical impulse duration. The given situation allows to model real communication systems.
- Selection of only one photon for impulse duration. This situation allows to estimate quantum cryptography efficiency protocol at malefactor with the ideal equipment, permitting to realize unauthorized data acsess presence.
Thus, spent researches allowed to estimate efficiency of quantum cryptography protocol BB84 at polarizing modulation usage.
The bibliographic list:
- Radio-electronic technologies of information safety: Collection of scientific articles / Under. edition. K.E.Rumjantseva. - Taganrog: TSURE, 2002. - With. 145-155.



